What Best Describes an Attack Surface
It is a metaphor used for assessing security in a hardware and software. Attack surface is the total sum of separate points which can be easily accessible for a hacker or attacker.
To protect files in case of a device is lost or stolen.

. Up to 30 cash back An attack surface is simply the number of possible ways an attacker can get into a device or network and extract data. But that is really just the sum of your organizations attack vectors. If a hacker wants to access the system he has to do by scanning the.
BUsers activities are logged to document incidents for security investigations and incident. An attack surface describes a view on a system that provides the sum of all vulnerabilities in the system that can be used by an unauthorised entity to insert data into modify or extract data. For organizations attack surface management means proactively addressing the cyber threats vulnerabilities and exposures that adversaries can use to gain unauthorized access to their.
It is the total number of attacks toward an organization within a day. In order to view this page correctly you must. An attack surface consists of all of the points of entry that hackers can use to access a system.
One major limitation of terrestrial microwave technology for use in long haul. A collection of connected Internet Protocol IP under the control of one or more network operators. Attack the Block.
In simple terms your attack surface is all the gaps in your security controls that. These include digital points of entry. Which option best describes defense-in-depth strategies.
The smaller the attack surface the easier it is to protect. The number of running services falls under the. An attack surface is the entire area of an organization or system that is susceptible to hacking.
They also include physical points of entry. Its made up of all the points of access that an unauthorized person could use to enter the system. It includes all vulnerabilities and endpoints that can be exploited to.
The attack surface of a system is the complete set of vulnerabilities that exist within that system. Identifies and reduces the amount of code and. They also must try and minimize the attack surface area to.
The set of points on the boundary of a system a system element or an environment where an attacker can try to enter cause an effect on or extract data from that. An attack surface is defined as the total number of all possible entry points for unauthorized access into any system. Learn more about threat attack surfaces why they are a top priority of.
A junior administrator ask you. Organizations must constantly monitor their attack surface to identify and block potential threats as quickly as possible. Simply stated the attack surface is comprised of the totality of an organizations network environment that an attacker can attempt to exploit to carry out a successful attack.
Which best describes the reason for encrypting offline files. Thats the idea behind attack surface the total number of points or vectors through which an attacker could try to enter an environment. An attack surface is the total sum of the vulnerabilities in a system that is accessible to an.
Once inside your network that user could cause damage by manipulating or downloading data. Terms in this set 4 Attack Surface. Weaknesses in the security posture such as weak passwords or unpatched software provide multiple avenues to attack the.
The term attack surface is sometimes defined as the collection of ways an organization can be breached. The attack surface of your organization is the total number of attack vectors that could be used as an entry point to launch a cyberattack or gain unauthorized access to sensitive data. This could include vulnerabilities in your people physical network or software environments.
The Attack Surface Attack Surface refers to the collective sum of all points of entry or interaction that are vulnerable to malware worms Trojans hackers you name it. A cyber threat attack surface refers to the digital and physical vulnerabilities in your hardware and software environment. AUsers and groups rights and privileges are checked to guard against creeping privileges.
The attack surface is the number of all possible points or attack vectors where an unauthorized user can access a system and extract data. What is available to be used by an attacker against the product itself. The smaller your attack surface the easier it is to protect your organization.

The Kidney Chart 20x26 Kidney Anatomy Medical Anatomy Anatomy And Physiology

Xd It Fits So Well I Know This Is Already On Here But It Fits So Much More Now Than When I Pinned It The First T Attack On Titan Funny

The Right Formula Aopa Angle Of Attack Private Pilot Formula

Tension By Letovbarski Artlab Origami Wall Art Paper Art Sculpture Paper Art

Eternal Love Poster Zazzle Com Love Posters Poems By William Shakespeare Love Me Quotes

Fun Fact Levi Is Actually Born On Christmas Attack On Titan Levi Levi Funny Funny Pictures

Understanding Stroke Chart Medical Technology Medical Knowledge Neurology

Hunter X Hunter Hunter Anime Life

Abyss Heralds Are Creatures That Are A Part Of The Abyss Order And Who Are Capable Of Manipul Fantasy Art Men Character Design Inspiration Creature Concept Art
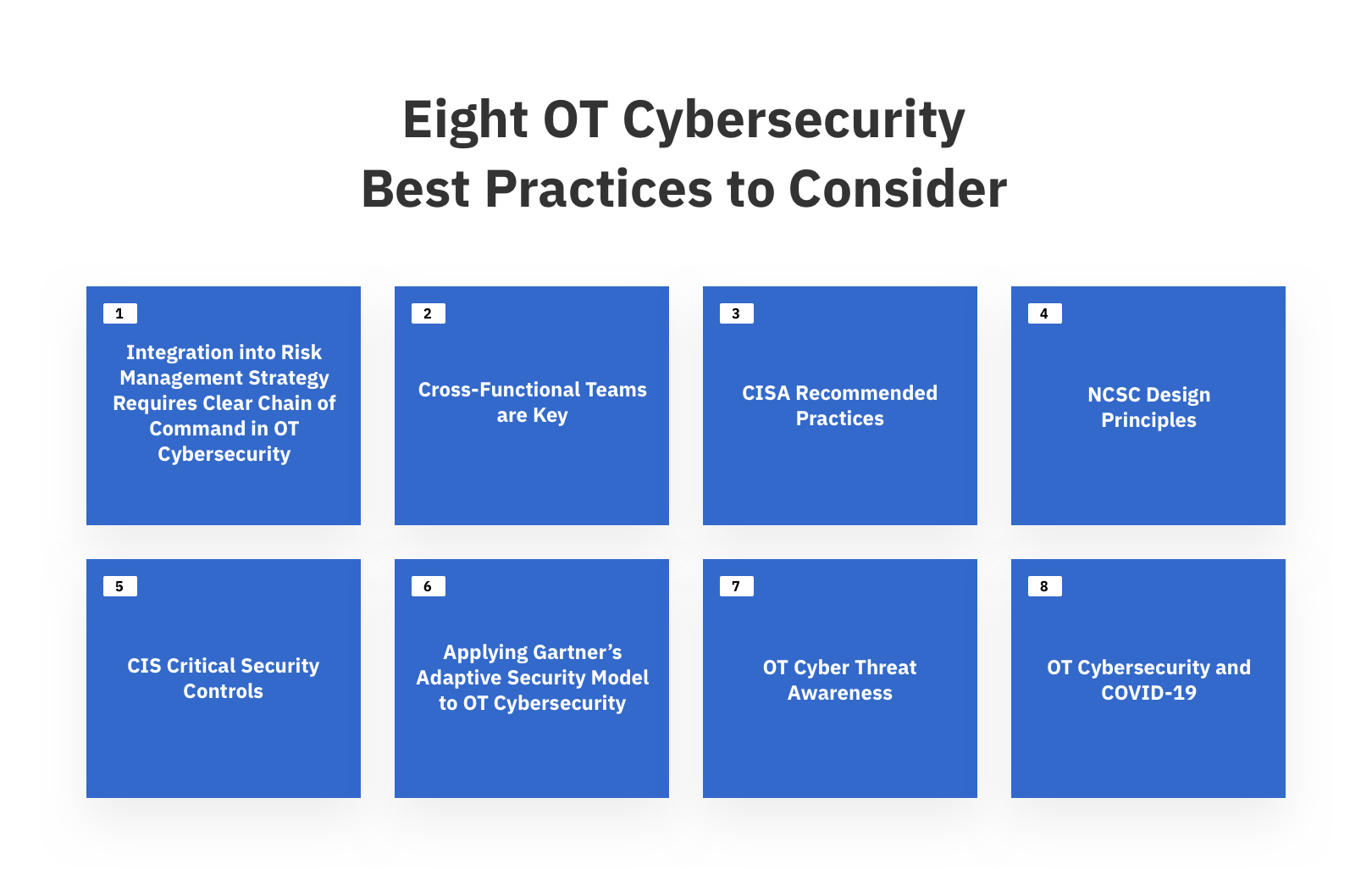
Cybersecurity Ot A Comprehensive Guide

What Is Footprinting In Ethical Hacking

Pin By Sheila Goddard On Inspiration Productive Things To Do Health Tips Adolescent Health

7 Types Of Cyber Security Threats

Ark Genesis Guia Mapa E Recursos Arkgenesis Guias Uncategorized Ark Survival Evolved Ark Survival Game Ark Survival Evolved Bases

Pin By Magda Van As On Learning Respiratory Therapy Medical Anatomy Nursing School Survival

This Is The Best Hockey Quote There Is No Better Quote That Describes This Sport Hockey Hockey Quotes Team Quotes




Comments
Post a Comment